Don’t be lulled into a false sense of security like our editor-in-chief, make sure your company and yourself are secure.https://www.chiangmaicitylife.com/clg/business/technology-digital/security-blues/
Posted by Citylife Chiang Mai on Friday, July 24, 2020
Unless one is filthy rich, a crime lord, or a celebrity, personal security isn’t something one thinks about beyond the common sense of being careful. Surely if one is sensible, then nothing bad will happen, right?
Wrong.
As some readers may recall, I recently had a lot of money stolen from my account. It still hurts…bad. While there isn’t much I can do about it now, since the thief managed to spend most of it on a gambling site, I am determined not to let anything like this happen again.
Last week, I reached out to a risk assessment firm called Dilis Risk MGMT, founded by an experienced security consultant and risk assessor. He spent 15 years working in China for various international risk management firms. He has worked with some of the world’s wealthiest people and a host of celebrities – sorry, can’t mention names but suffice to say I was impressed. Let’s just call him, ‘Mr. X.’
What I learned about my lack of security was pretty shocking and has made me realise that there could be many of you out there in the same shoes. While I am not wealthy like any of his previous clients, Mr. X insisted that I realise that I, too, had to take my personal security more seriously.
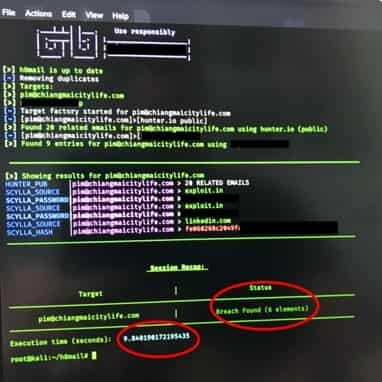
First of all, we met at the Citylife office, which he promptly, and rather upsettingly, broke into with ease. It then took me less than two minutes to break into my office after he showed me how – which was alarming. Once inside, he then turned on my computer and, within minutes, read out two of my passwords – which was terrifying. I thought I had been quite cunning, writing numbers out on a word document in Hebrew or Thai letters, and mixing them with important dates in my life. Apparently not.
Mr. X learnt Mandarin, and it was this language skill that opened the door to working with China-based European risk assessment companies. He received training from both military and intelligence organisations worldwide, including, for example, hostile environment training. This led to consulting with large organisations on their security requirements, much international travel with the crazy-rich, and being hired by Hollywood studios to ensure their stars’ safety while travelling.
Besides personal protection, he spends his time looking for weaknesses and risks for companies and high-net-worth individuals. In recent years, his interest has moved towards cybersecurity.
“Physical and cybersecurity need to overlap, converge and communicate,” said Mr. X. “People aren’t doing that, and that is often the weakness of many companies and individuals. If you can get physical access to a computer, then it is easy to commit cybercrimes.”
“Security is all about by layers,” he explained. “First, you look at the location, then physical access. Where and how do people access the building? How easy is it to get in at different times of the day? How do the staff or other authorised people gain access? Then you look for CCTV or other monitoring devices and where they are placed.”
“Often, people waste resources by putting the cameras everywhere, even though they never have time or resources to monitor dozens of screens. It is best to be strategic in camera placement. Even so, if you have cameras in plain sight, it is always possible for criminals to avoid them. So, set up a backup system with less-obvious, hidden cameras in different locations. Better yet, with different power sources or communication methods, so it can’t all be jammed with off-the-shelf signal jammers.”
“If you are a company, then security has to start at hiring. I have a personality test I ask my clients to use as part of the interview process. It helps filter out some character traits which may be undesirable. Next is access control; who has keys, passwords, physical access? People may feel they have security already, but I often find that they are not using their assets correctly. This can create a risk or flaw that can be exploited. Start on the outer layer, and you slowly work your way in.”
I looked over to see Mr. X fiddling on his laptop. The next thing I knew, he showed me how hackers execute a phishing attack on a social media platform. Which one? The one beginning with F…and within minutes, he was able to reveal passwords and account information – it was disconcerting.

“People think that they have nothing to hide,” Mr. X continued. “But no one should be blasé about security. Even if you think you have nothing to worry about or be embarrassed about, what if an attacker can use your accounts against your less tech-savvy contacts? Because they trust you, when they receive something (apparently) from you, happily open an email or click a link?”
“The current world and economic situation means that there are is an increasing number of desperate people out there globally. Unprotected technology means an easy way to make a quick buck.”
“All it takes are some basic safety measures, and you can feel more assured that you are not the easiest target. Often, that is all it takes for an attacker to move onto a softer target.”

Mr. X offers individuals and companies risk assessment consultations that include exciting services such as a physical penetration test where he attempts to breach your security to provide you with tools to shore up that breach.
“I find it incredible that some places have a better lock on their toilet doors than their business’s front doors,” he said, giving me a look that I couldn’t miss. Note to self: get new office locks (…and we have).
“One thing I have been shocked at here in Chiang Mai is talking to many bar and restaurant owners who have said that they expect parts of their income to disappear through theft. This is not acceptable. There are ways to make sure that you don’t bleed as a business, and I am here to help people put that in place.”
“A risk assessment will identify strengths and weaknesses in the security setup, very often identifying weaknesses of which the client was not aware. The assessment will also give the client a much better understanding of the processes that make good security effective.”
Mr. X has been in Chiang Mai for a year and a half now and hopes to make it his home. Please feel free to get in touch with him for your security needs. You might be surprised how exposed your information is!
Some Basic Tips from Mr. X
- Enable two-factor authentication on all accounts that offer it. Consider any other security options they offer also.
- Ensure none of your internet-connected devices are using default passwords and usernames (as a list of these is available for anyone to download and use in an attack). This goes for every device you have connected. There are websites that show/give access to unsecured devices such as poorly installed CCTV camera systems. There is no notification for the user that their devices are being broadcast online, such as Shodan, the search engine for devices connected to the internet.
- If your wifi password is your phone number, or something similar, change that as after the AIS leak a list of customer numbers is available for download. Phishing/social engineering attacks will likely use data from the AIS data dump.
- Covid tracing may be used as a premise in a social engineering attack. For example, you’ve recently posted somewhere on social media about a trip or checked in somewhere. The attacker calls you stating you were at such and such a place on whatever date and to confirm/discount any risk they will SMS you a link to sign into something or other. This is very simple but one that may work on a certain number of people.
- Chances are you have had some passwords leaked in the past. So if you receive an extortion email that provides a password (more than likely an old password), the attacker hasn’t gained access to your device. They are merely using a data breach dump.
- If you tend to overshare on social media, understand what can be done with that info. Understanding the risks will help you to think about what you post. For example, a genuine recent post in a Chiang Mai Facebook group from early this year:
- Just moved to CM. Looking to buy a good car/truck/SUV or possibly long term lease. Please PM me. Baht 750,000.
- What I have gathered from looking at this post and his profile is the following:
- He is elderly and lives with his wife.
- He is oversharing.
- He has not procured a loan of 750,000 as he just moved here, and it would be impossible for him to do so. Therefore he is cash-rich.
- To proceed, I would engage in messaging, arrange a meet, and have an accomplice follow him to his home.
- I would then have my accomplice call him and arrange to meet under the presence of showing him a car to rent. I then know that either his wife is home alone (chances are they haven’t made many new friends here as they have just moved) or accompanied him.
- Either scenario works for the offender who can enter the property with lower risk and look for the money or other valuables.
